Table of Contents
- 1. Locate the Security Group of your EC2 Instance
- 2. Edit the Inbound Rules
- 3. Add a Rule for ICMP
- 4. Test the Ping
- 5. How can I always Ping Outside from EC2?
- 6. Keep Security in your Mind
- 7. What if Ping still does not Work?
When you launch an Amazon EC2 instance, you might notice that by default, you can’t ping the instance’s public IP address from outside sources or even from the very same EC2 instance you just created. This is because of the security group settings in AWS that prioritize security and block ICMP traffic, which enables PING. However, there are times when you need to make your EC2 instance pingable, whether for testing or some specific use cases. Here’s a step-by-step guide on how to make AWS EC2 public IP address pingable.
1. Locate the Security Group of your EC2 Instance
On the EC2 dashboard, locate the “Instances” link on the left-hand side. Click on it, and you’ll see a list of your instances. Choose the instance whose public IP you want to make pingable.
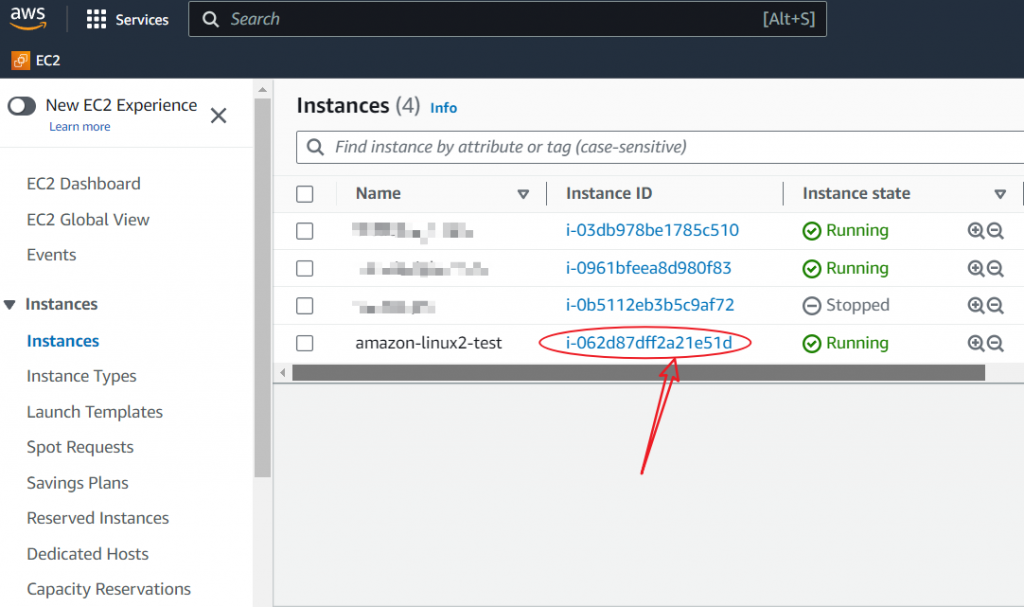
Once you’ve selected the instance, look at the bottom for the “Security” section. You’ll see the name of the security group associated with your instance. Click on the security group ID.
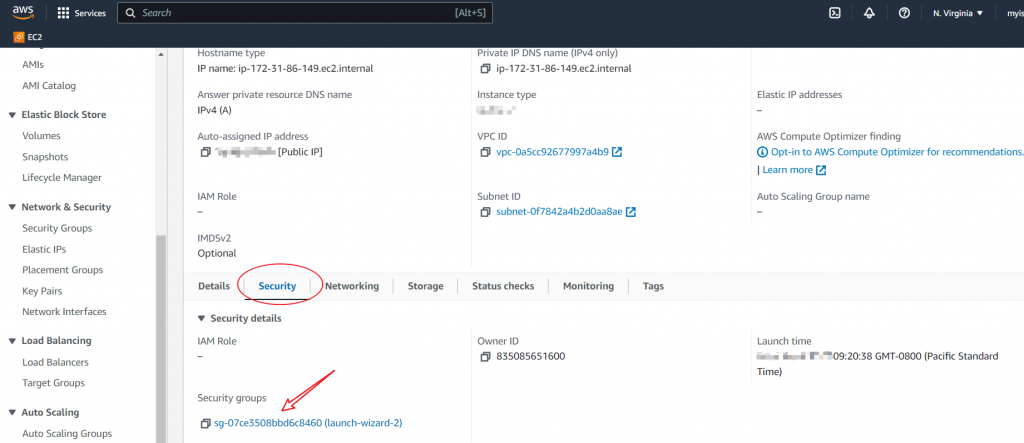
If you see multiple security groups at this point, this instance has multiple network interfaces. Then, navigate to the “Networking” Section instead. Select the security group ID of the network interface, which is associated with the public IP address you would like to ping.
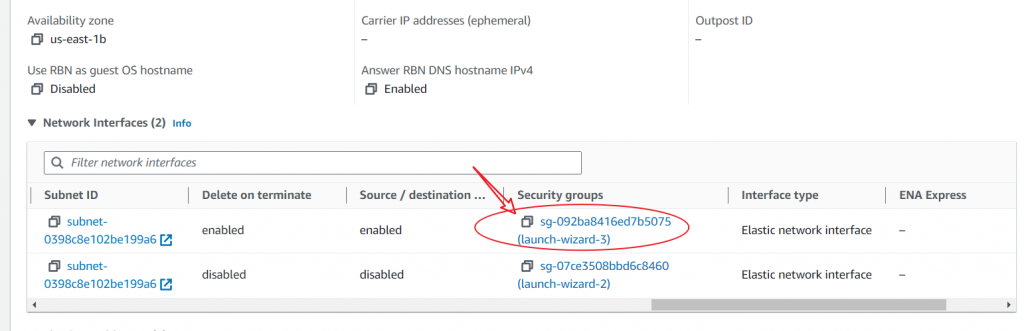
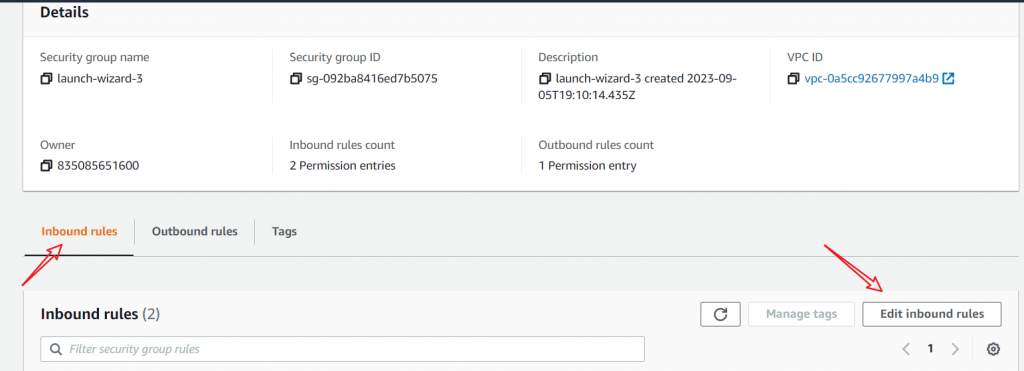
2. Edit the Inbound Rules
Now, click the “Inbound rules” tab. Then, select “Edit inbound rules”.
3. Add a Rule for ICMP
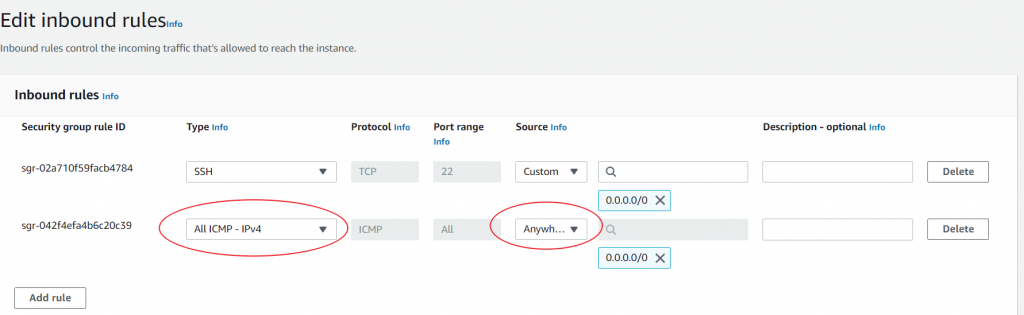
3.1 Allow All ICMP
Click the “Add rule” button. A new rule row will appear.
- For the “Type” field, select “All ICMP – IPv4” depending on your console’s version).
- For the “Source” field, select “Anywhere” to allow pings from any IP. For a more secure setup, specify a particular IP or range.
Click the “Save rules” button once you’re done.
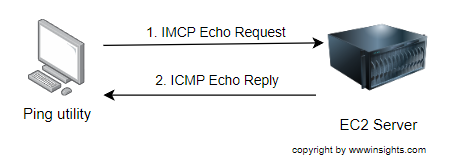
3.2 Allow ICMP Request
You can only enable ICMP’s echo request if you do not want to enable all ICMP protocols. As shown in the below figure, the ping utility initializes an ICMP echo request packet to the EC2 server. As long as the security group allows the ICMP echo request packet to go through, ping shall be able to work.
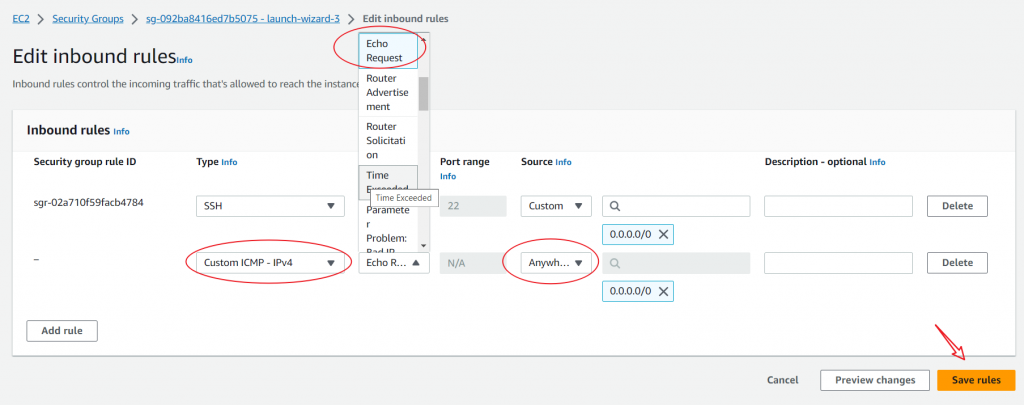
As shown in the diagram below, choose Custom ICMP – IPv4 and Echo Request as the protocol; Choose Anywhere as the source. Then, click ‘save rules’.
4. Test the Ping
Now that you’ve updated the security group rules, you can ping your EC2 instance’s public IP address. From an external machine or the same EC2 instance, run:
ping your_EC2_public_IPIf everything was configured correctly, you should start receiving ping responses.
5. How can I always Ping Outside from EC2?
Wait a minute. When we first create an EC2 instance, we can ping the outside world from the EC2 instance, and we do not need to explicitly configure to allow Ping ICMP echo reply to pass the inbound rule. How does that work? Let’s discuss it in depth.
When we send an ICMP echo request (ping) from the EC2 instance, it’s considered outbound traffic. The outbound rules of our security group typically allow this.
When the external host sends back an ICMP echo reply, it’s essentially a response to the initial request made by the EC2 instance. AWS and many other firewalls or security platforms use “stateful” filtering. This means that when you initiate a connection (or send a request) from within the EC2 instance, the firewall/security group keeps track of this connection state. Because of this stateful property, the response (ICMP echo reply in this case) to the original request is automatically allowed, even if there aren’t explicit inbound rules to permit it.
In simpler terms, since the EC2 instance initiated the request, the security group knows to expect a corresponding reply and will allow it through, regardless of the inbound rules.
6. Keep Security in your Mind
Remember, making your EC2 instance public IP address pingable can expose it to certain threats or unwanted traffic. Always tighten the security as much as possible based on your use case. If you’re only testing, it’s a good practice to remove the ICMP rule from the security group once you’re done to keep your instance secure.
7. What if Ping still does not Work?
What if Ping still does not work after you get the security group inbound rule taken care of? There must be somewhere else to continue to block ICMP packets. Please continue to check ACL or other firewalls you may have in the system.
That’s it! You’ve made your AWS EC2 public IP address pingable with just a few clicks. Feel free to access more AWS blogs on our website.
[Credit: Featured image is proudly generated by Midjourney]

